Vulnerability
In this section, you will find information about Horusec-Vulnerability service.
What is it?
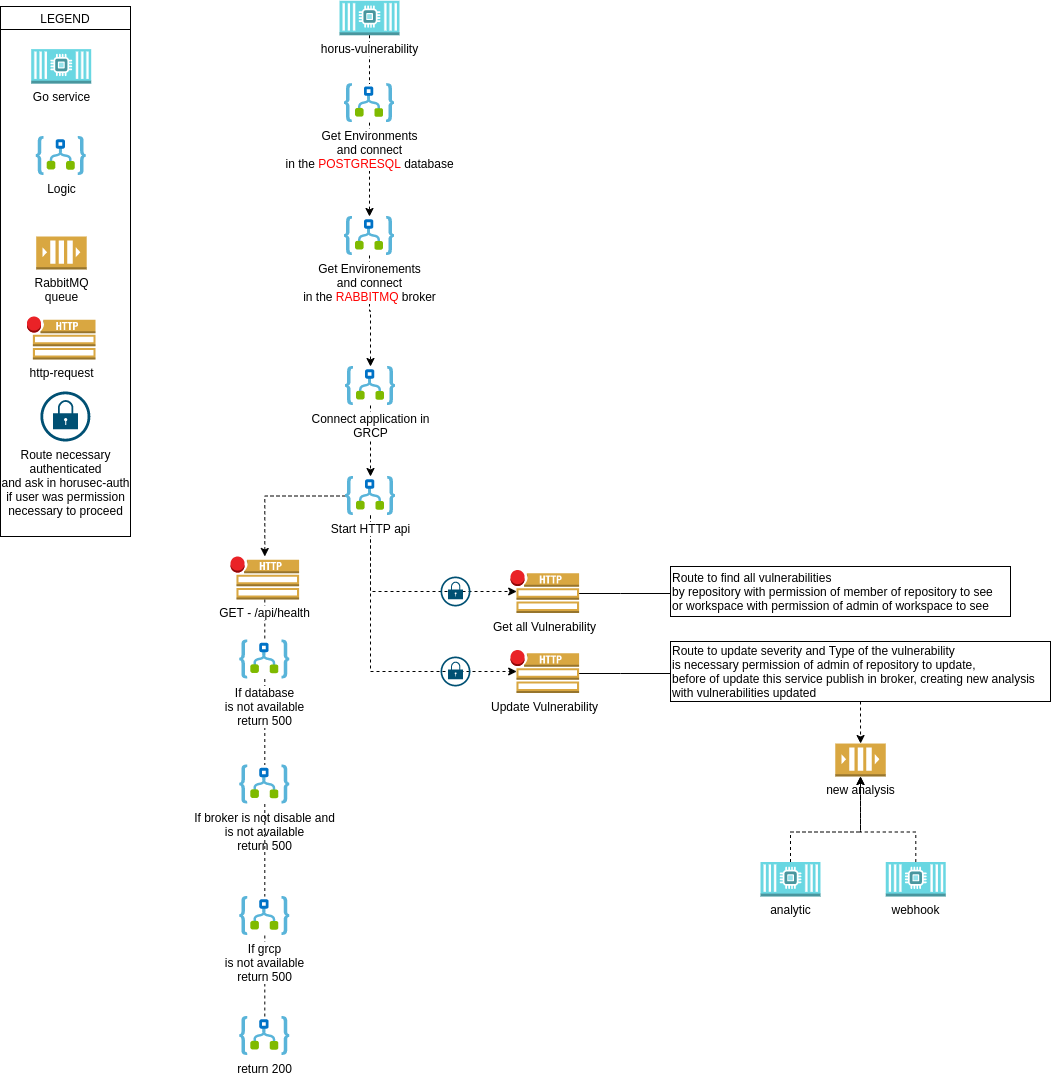
Horusec-Vulnerability performs the manages the vulnerabilities found in the analysis.
Requisites
To run this service locally, you need:
- PostgreSQL (with the applied migration);
- RabbitMQ;
- Horusec-Auth;
- Golang.
Installation
Step 1: Install dependencies:
go get ./...
Step 2: Run the service with the command below:
go run ./vulnerability/cmd/app/main.go
It will return this log:
service running on port :8001
swagger running on url: http://localhost:8001/swagger/index.html
Environment variables
These are the possible environment variables you can configure in this service:
| Environment Variable Name | Default Value | Description |
|---|---|---|
| HORUSEC_SWAGGER_HOST | localhost | It gets which host will be available in the swagger. |
| HORUSEC_DATABASE_SQL_DIALECT | postgres | It gets the dialect to connect to POSTGRES database. |
| HORUSEC_DATABASE_SQL_URI | postgresql://root:root@localhost:5432/horusec_db?sslmode=disable | It gets the URI (Uniform Resource Identifier) to connect to POSTGRES database. |
| HORUSEC_DATABASE_SQL_LOG_MODE | false | It gets the value to enable logs on POSTGRES. |
| HORUSEC_PORT | 8008 | It gets the port the service will start. |
| HORUSEC_BROKER_HOST | 127.0.0.1 | It gets the host to connect to the RABBITMQ broker. |
| HORUSEC_BROKER_PORT | 5672 | It gets the port to connect to the RABBITMQ broker. |
| HORUSEC_BROKER_USERNAME | guest | It gets the username to connect to the RABBITMQ broker. |
| HORUSEC_BROKER_PASSWORD | guest | It gets the password to connect to the RABBITMQ broker. |
| HORUSEC_HTTP_TIMEOUT | 60 | It validates the time in seconds to wait the response for a HTTP request. |
| HORUSEC_GRPC_AUTH_URL | localhost:8007 | It gets the horusec-auth URL connection with the GRPC. |
| HORUSEC_GRPC_USE_CERTS | false | Validates if the certificate use on GRPC is enabled or not. |
| HORUSEC_GRPC_CERT_PATH | It gets the path of GRPC certificate. |
Read more
Feedback
Was this page helpful?
Glad to hear it! Please tell us how we can improve.
Sorry to hear that. Please tell us how we can improve.
Last modified August 13, 2021: Changes in the documentation (#105) (89d826da)